Table of Contents
Introduction.
We have already seen the growth rate of the cybersecurity domain and their attacks in recent years, and to overcome this we have discussed how to prevent these types of cyber-attacks through our article antivirus vs firewall.
In this article, we are going to tell you each and everything about firewalls and different types of firewalls, the aim is to deliver such content so that you don’t have to read it again elsewhere.
What is a Firewall?
To protect a computer or a device we need an antivirus, likewise to protect networks of computers or networks of devices we need a firewall.
We access the internet at home, schools, colleges, or offices, these internet comes to us through internet service providers.
The internet is a huge connection of devices globally, that is whatever devices are there on this planet it is connected to the internet.
So there are a lot of many and unknown devices out there which we don’t know what it is used for.
In this interconnection of such a huge network, It becomes an utmost priority to secure our device as we don’t know from where the data is coming and for whom it is coming.
The ISP’s sends us the internet directly as they received, meaning along with their internet comes to every type of data package from authenticated as well as the unauthenticated source.
So if we use this internet directly without knowing it’s the source or to be more specific without knowing its content what it contains, whom it is for, what this packet will do once it is on our local network, it becomes a high risk and each device on the network get vulnerable to cyber-attack.
Therefore in order to check the contents of a coming network and its history we set up a firewall.
Firewalls are set up at the doorstep from where we access incoming network (The internet) and these firewalls constantly scan the incoming and outgoing data packages from our local network to the internet.
And if they found some suspicious packets or malicious activities within the network it immediately discards or terminates the package or activities respectively.
Understanding it through a live example.
Think of a house where you live during the COVID-19 pandemic.
Now lockdown has been imposed in your town and you can’t go out for your essential supplies, now the government has arranged some delivery supplies from local grocery stores or supermarkets.
All you have to do is to order your requirements and those delivery guys will bring you the stuff.
Now you don’t know from where they are bringing these supplies and if it is sanitized properly or not.
So you set up a security guard at entry of your house or apartment, now this security guard receives your supply from delivery guy and scans it through a scanning gadget you have provided to him/her, to check if it is contagious, where it’s coming from, it’s a destination and many more.
Now in this scenario, the house is your local network, people within the house are devices, supplies you request from outside are data packages, delivery guys are internet service providers, grocery or supermarkets are unknown network or server from where data packets come, a security guard is the router and scanning gadget is the firewall which checks the packets.
Now by this time, you may have got a clear idea about the firewall.
Each firewalls working and its types are different based on the user’s requirement.
Type of Firewalls.
Based on the working are a requirement of user and organization we can set firewalls and configure it to our choices.
In these sections, we are going to each type of firewall in a detailed manner so that one does not need to read it again elsewhere.
- Packet Filtering Firewall
- Circuit Level Gateway Firewall
- Stateful Inspection Firewall
- Application Gateway or Application Level Gateway Firewall
- Next-Generation Firewall
Packet Filtering Firewall.
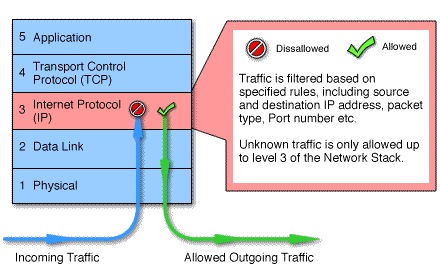
In a packet filtering firewall, the core principle is that each packet is scanned in isolation about their IP address, ports used to source and destination of the packet and based on certain rules you set for filtering the packet may proceed or gets discarded.
These firewalls are mostly set up within your router and it constantly scans your data packets within the router.
All the internet transmission follows TCP/IP (Transmission Control Protocol/Internet Protocol), according to these protocols whatever data transmission is happening have a unique address.
We call it an IP address, and this transmission takes place through ports, now ports are numbers assigned to specific services which tells that packet following this port belongs to this service.
For example, a packet following port number 80 must be a packet of the HTTP protocol, as port 80 is reserved for HTTP services.
IP addresses and ports work together to deliver a packet, for example, you put the request to the web browser a Facebook page then if an IP address of Facebook is 192.168.0.2 and port 80 is used then your router will get a data packet of 192.168.0.2:80.
So you see how ports are specified after semicolon with IP address.
It this combination that makes packet filtering firewall works.
There are lot many numbers of ports for transmission and n numbers of IP addresses out there, if you are using packet filtering firewalls you can set up rules to block certain IP address with these numbers of ports and your router will scan each packet, and if it found your request it will block that packet from entering your network.
This seems easy and fun, but a person with a good understanding of firewalls and ports can easily bypass your firewall, and this is how.
IP spoofing.
All your firewall does scan the IP address and ports, and based on the outcome it decides whether to proceed or discard.
Now in IP spoofing the sender of the packet (hacker) insert a fake IP address which your firewall permits, and this way they are able to get through your network.
Source Routing Attacks.
In this attack, the attacker specifies another port within the packet to take while encountering a firewall, this port which the hacker specifies does not match the service of the port and data within the IP address.
Meaning you could request for an SMTP service which is a 465 port number and is not blocked by a firewall, but an attacker may send you some other file through this port number.
Along with these drawbacks of packet filtering, it is widely used to date because of its simplicity and ready-to-use service.
Some router provides a built-in packet filtering firewall as this is the first or primary mode of protection towards ant cyber-attacks. Reasons to use packet filtering is
- These are efficient
- It is the fastest mode of protection
- Completely transparent to the user
- Can be changed according to users need
- It is inexpensive.
Circuit Level Gateway firewall.

A circuit-level gateway works at the session layer of the OSI model.
In this method, a circuit-level gateway monitors the TCP handshaking of data packets between the client and server to determine if the session is legitimate or not.
Working:- A client request gateway to establish a connection for data transmission, the gateway then on behalf of the client opens a connection and closely monitors the TCP Handshaking between client and untrusted server.
The handshaking took place in three steps, which involves the exchange of TCP packets that are flagged SYN (Synchronized), SYN-ACK (Synchronized Acknowledged), and ACK (Acknowledged).
Circuit level gateway allows connection only when these exchange of packets are sequential, logical, and if follows some legitimate rules.
Since these types of firewalls do not actually monitor the packet, these are considered as the fastest mode of connection.
They do not inspect packets themselves.
Therefore this type of firewall that does not check packets directly can cause malware to enter your personal network.
Therefore it is not recommended to use this type of firewall within organizations or banking or at high-risk sectors.
Stateful Inspection Firewalls.

This firewall is considered as the combination of both other two types of firewalls that is packet filter and circuit-level gateway.
This firewall not only examines the packets in isolation but also monitors the TCP handshake between client and server to see if the packet delivering to the network is legitimate or not.
This firewall keeps the track of network connection that is TCP or UDP and also able monitors each package attribute during a connection in its memory.
The attributes which are within memory, are also known as the state of the connection and include IP address, ports involved, TCP handshakes.
It monitors the incoming and outgoing packets as well as the state of the connection and stores these results in dynamic state tables, therefore it is also known as dynamic packet filtering.
If no packet exchange occurs for a certain amount of time period, the state connections are removed from the state table, and connections are terminated.
Therefore to tackle this situation applications sends keepalive request periodically so that firewall does not terminate their connection automatically.
Stateful inspection firewall process application layer, so it has a clear picture of what’s going on behind the curtains therefore it is more secure than packet filtering firewall.
In stateful inspection, there is a thin line between the performance of the packet and the security of the application because both perform pretty well.
However, due to packet filtration, there is performance degradation. Also due to the state table which is maintained logically may sometimes cost memory and processor power.
Fine control of application proxies is lost due to the demand for better performance, but this doesn’t concern the usage. Although a lot of companies use this firewall, it is also a bit expensive for personal usage.
Application Gateway Firewall.
Application Gateway firewall also known as the application-level gateway firewall operates in the application layer of the OSI model and is considered as one of the most secure firewalls out there.
This firewall high-level network security firewall for servers as well as clients.
Working:- If a user wants to access some files, web pages, or data from the server, then clients first get connected to the proxy server, which then establishes the actual connection with the main server.
As already told that this firewall resides in clients as well as servers side.
Therefore, the proxy server hides IP addresses and other secured information on behalf of clients, which total results in a computer internal system may communicate with the external system without clients’ knowledge or proxy server.
Since this firewall consumes a lot of processes it can be a bit slower than the rest of the firewalls.
Sometimes this firewall is used with some other firewalls and may work parallel with them, which means they sit behind and act as the second layer of protection.
If the packet passes through the first firewall then it will be examined by the application gateway firewall.
Next-Generation Firewall.

While previous firewalls provide protection to packets, communications, incoming and outgoing packets, and some typical states, these firewalls will provide protection beyond traditional usage.
It may include features like application awareness, access control, integrated intrusion control, and cloud-delivered protection.
Some common features may also include deep packet inspection meaning checking the actual content of the packet, TCP handshakes, or maybe a state inspection table.
But yet it is an assumption about the next-generation firewall. As we all know necessity is the mother of invention, which might trigger the idea of inventing this type of firewall.
How to Choose the Correct Firewall.
Choosing a correct firewall depends on a lot many factors.
You need to ask yourself for what purpose it is needed, what we need to protect because in an organization or a company there are a lot of work-related data and personal pieces of information of employees.
While for a personal network there aren’t any documents to protect however your personal data are your asset in this era so a firewall is a must for all.
Also if you are a single user an antivirus will be enough for you instead of a firewall.
Questions you should be asking yourself.
- What are the technical requirements of a firewall, and an alternate product works better at this level?
- What we need to protect is an organization or low visible information on the internet.
- If it’s necessary for my personal network what type of firewall will work for me? Typically a packet filter firewall is enough for a single user.






